CyberSploit2 CTF — Vulnhub walkthrough
In this guide I’ll go over the steps to get root access in this VM.
You can download the VM from: https://www.vulnhub.com/entry/cybersploit-2,511/
Once it’s running in VirtualBox, I run the usual netdiscover to get the IP address of the machine:

After that a quick NMAP will reveal that it has SSH and HTTP open:

The website on port 80 is just a leaderboard:

The page’s source code hint’s “ROT47”:

We google a bit for an online rot47 encoder/decoder:

And we get:

Now that I have two values, I’ll try to use them for SSH:
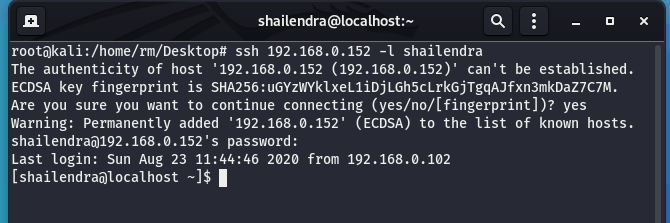
The home folder has a file called hint.txt with the message “docker”

Docker IS running in the server:

Because the current user is in the “docker” group, it can run without sudoer permissions, this allows us to escalate privileges:

I’ll run the base docker image, mounting the root folder of the host as a folder in the container, then chroot to it, this will end up containerizing the host system but with root permissions:
docker run -v /:/mnt --rm -it alpine chroot /mnt bash

And now that we are root we can move freely:

And that is all for this short challenge!
